Mobile App Security and Protection
Secure the mobile apps you create with Mobile Application Security from Digital.ai
Protect the mobile apps you create through obfuscation of code, anti-tampering, and other app hardening techniques.
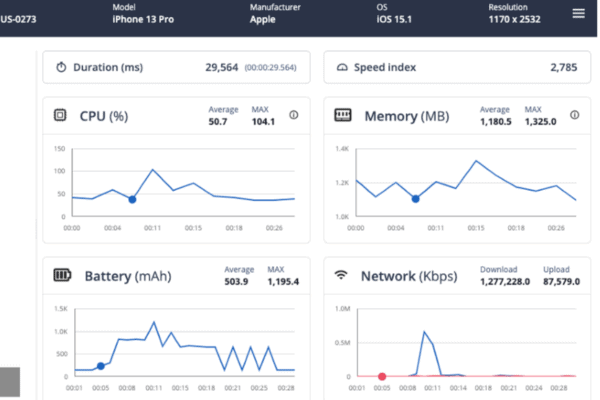
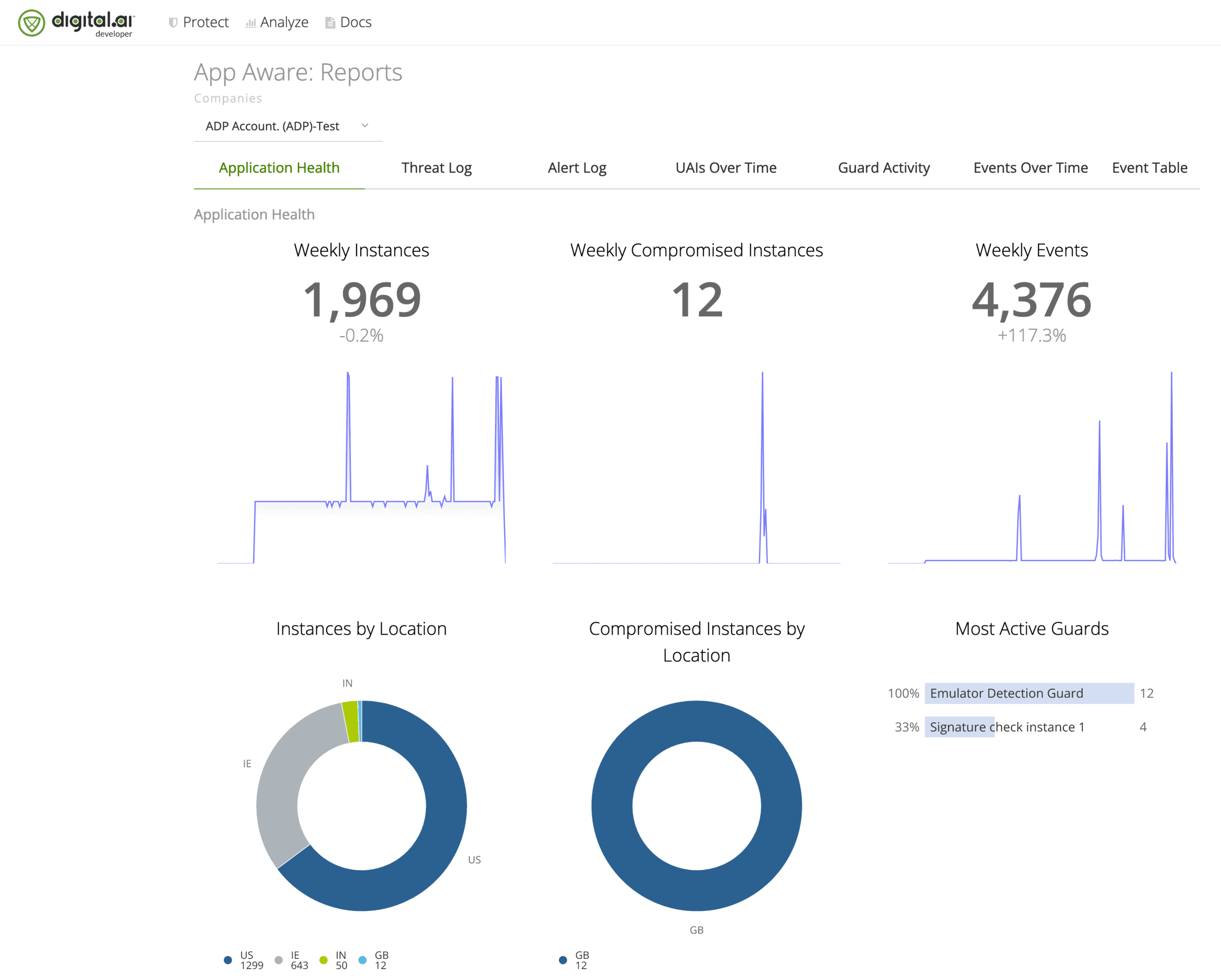
Monitor threats to those apps. Automatically react to app attacks by building Runtime Application Protection (RASP) directly into your apps.
Protect, Monitor, React
Enhance your mobile app security by inserting protections into mobile apps at build – without slowing down development. Monitor threats to the the apps you give to your customers. Integrate monitoring capabilities with your existing SIEM. Automatically react to app attacks through Runtime Application Self Protection (RASP). Prevent applications that are not protected from being released into production.
Build Secure Mobile Apps to Prevent Reverse Engineering
Exploiting Your App Code is Easier Than Ever
Threat actors are better organized and have access to more funding than ever. They can tamper with your apps using any of the following easily available tools:
Jailbroken Device or Rooted Device
Jailbreak and Root “Communities” of hackers share tips, tricks and techniques for breaking free of restrictions that Apple and Google place on iOS and Android devices on various easily discoverable forums throughout the internet.
Decompiler
Dozens of popular tools are used by Computer Science students, hackers, and threat actors all the time. Most of these tools are freely available and legal to use for legitimate purposes but can easily be used to reverse-engineer the apps you create and give to your customers.
Emulator
Emulators allow students, hackers and threat actors to run apps intended for use on mobile devices on PC and Mac OSs for a variety of use cases. Threat actors regularly avail themselves of emulators to test various attacks on mobile applications.
Debugger
Debug tools such as Chrome DevTools, Bugsee, Instabug, Xcode are available to download and are invaluable for developers and threat actors alike.
How to Protect Your Apps
Code Obfuscation
Code obfuscation reorders and reconfigures the machine or source code at compile, making it harder for threat actors to read and, thus, harder for them to exploit.
Live Monitoring
Automated reporting and alert mechanisms show App Owners whether, when and where their app is being run in a compromised or unsafe environment.
Real-time Responses
Swiftly react to attempts to compromise your app with custom actions, such as forced authentication and anti-cheat mechanisms.
Capabilities
See why you need application hardening as part of your DevSecOps strategy!
Related Products

Mobile App Security and Protection
Want to learn more about how Application Security will benefit your organization?